Prioritize security now for a worry-free future
Today, maximum care is required about what material we consume online. Just opening the link can compromise personal data.
If you suspect or have been scammed by someone into sending them money, call us on 00355 4 2381 381.
Below you will find the most important tips for navigating the online website

The bank will never ask you for confidential information over the phone
One of the prevalent deception techniques recently employed by individuals or various criminal groups online is "vishing." Vishing, a shortened form of "voice phishing," relies on manipulating individuals through phone conversations or voice messages, convincing them to provide fraudsters with access to their devices, download applications infected with malware, or disclose confidential personal information such as login credentials, debit/credit card details, or other sensitive financial data.
Vishing scams often have the objective of financial gain. By tricking you into revealing confidential information such as usernames and passwords, criminals can gain unauthorized access to your bank account and carry out unauthorized transactions.
Be vigilant and follow the following advice to avoid falling victim to these fraudulent schemes:
Exercise caution when someone calls you claiming there is an urgent situation.
In such cases, remain calm, avoid hasty actions, and never provide sensitive information over the phone. Fraudsters often try to create a sense of urgency to prompt you to hurry and share sensitive information or grant them access to your device
Be cautious if someone contacts you unexpectedly.
Be cautious if someone contacts you unexpectedly, claiming to be from your bank or a financial institution, and requests sensitive information. Raiffeisen Bank will never ask for your password, PIN, or the three-digit CVV on the back of your card over the phone or any other confidential information.
Always verify the caller's identity if you receive an unexpected call.
Vishing scammers may call, presenting themselves as representatives of a legitimate organization and may use techniques to make the displayed phone number look like an official number of a company. Do not trust a person solely based on the legitimacy of the phone number. If you were not expecting such a call or the content seems suspicious, take their name and department and request to call them back through an official company number.
Use two-factor authentication (2FA) whenever possible.
2FA adds an extra layer of security by requiring a secondary verification step, such as a one-time code sent via SMS or email, helping protect your accounts if your password is compromised.
Do not allow individuals who contact you unexpectedly to trick you into downloading software or taking temporary control.
Do not allow individuals who contact you unexpectedly to trick you into downloading software or taking temporary control of your computer under the pretext of removing malware or fixing a technical issue.
Trust your instincts.
If you suspect that a call might be a vishing scam, hang up. If you want to confirm the legitimacy of the call, go to the organization's official website and use the contact number published there to communicate with the organization.

Ensure the security of your mobile phones.
Mobile devices have become an indispensable part of our daily lives. In these devices, we store personal, financial, and business information, among others. If the device is lost or stolen, all this information is at risk. Also, if your device is not properly secured, malicious individuals can access all your data: photos, contacts, text messages, documents, etc.
Extra caution should also be exercised with the applications you download on your phone. Applications may contain malware and steal sensitive data from your mobile devices (such as photos, internet activity, emails, contact lists, documents, etc.). They may even intercept SMS messages that your bank sends to identify you. These applications can also spy on you by using the microphone and camera or record your phone calls.
Protect yourself and your personal and financial data by following these simple steps:
Secure your phone with a unique and strong PIN or password (at least 6 characters) to prevent unauthorized access.
If possible, use biometric authentication methods such as fingerprint recognition to securely unlock your phone and banking applications.
Activate automatic updates for the operating system and installed apps on your phone to avoid security issues.
Regularly check for updates to the operating system and installed apps on your phone and apply these updates if they are not applied automatically.
Keep your mobile devices with you at all times or store them in secure places.
If possible, encrypt your devices to prevent copying and reading of data even if the device is lost or stolen.
Download mobile applications only from the official app stores, such as Play Store for Android devices and App Store for iOS devices.
Read user reviews as they often serve as a good indicator of potential problems a mobile application may have.
Check the permissions requested by the application. Be vigilant, and if the application prompts you for approval for an access right that seems inappropriate, do not approve it. If an application has permissions to access the camera, microphone, location, memory, etc., it may collect data that it could send to the application provider.

Avoid using public and insecure Wi-Fi.
Public WiFi networks, such as those found in cafes, pose considerable risks to your internet security, especially when conducting banking transactions.
Falsifying a public WiFi network is not very difficult. As soon as you connect to such a network, all the information you send can be intercepted, including emails, passwords, debit/credit card details, online banking transactions, photos, etc.
Follow the advice below to stay secure while using public WiFi:
Disable the configuration that allows your devices to automatically connect to nearby WiFi networks, as you may unintentionally connect to insecure networks.
Avoid actions that pose a risk while connected to a public network, such as logging into your bank account or conducting financial transactions.
If using public WiFi is unavoidable, use Virtual Private Network (VPN) services to secure communication and protect your data.

Always use a strong password and, whenever possible, enable two-factor authentication.
Passwords are the most common form of user identification used by computer programs. As such, they represent a particular interest for various malicious actors who, if they manage to find your username and password for an application, can log in and perform actions under your identity.
Certain individuals or groups may use various tools to find someone's password. One method involves using a list containing the most common passwords, dictionary words, and weak passwords. An 8-character password consisting of numbers and uppercase and lowercase letters can be cracked in a matter of minutes if the application does not have protective measures.
Therefore, it is crucial for passwords to be long and not contain dictionary words in foreign languages to make them difficult to find. For example, a strong password would be: D0n0tshareyourcredent1alsw1thothers!
Also, be cautious not to reuse passwords to log in to multiple applications or devices. If one of these applications is compromised, attackers can gain access to all other applications and devices where the same password is used, potentially reading, copying, publishing, modifying, and deleting all your data.
Most importantly, use two-factor authentication (2FA) whenever possible. 2FA adds an extra layer of security by requiring a second verification step, such as a one-time code sent via SMS or email. Thus, even if someone manages to find your password, they won't be able to access your account without the second factor, significantly reducing the risk of unauthorized use of your applications and devices.

Protect your online identity - be cautious of fake websites.
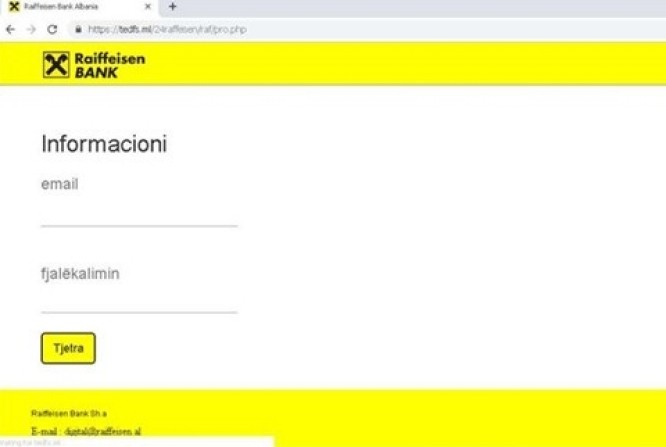
Individuals and online criminal groups often send phishing emails that contain links leading to fake websites mimicking well-known sites, such as a bank's website. These fake sites can appear almost identical to the real ones, making it difficult to distinguish. Any information you enter on these sites becomes accessible to the deceptive party. Once you enter your login credentials on the fake site, the deceivers can use this information to access your bank account and perform financial transactions under your identity.
Protect yourself with these simple steps:
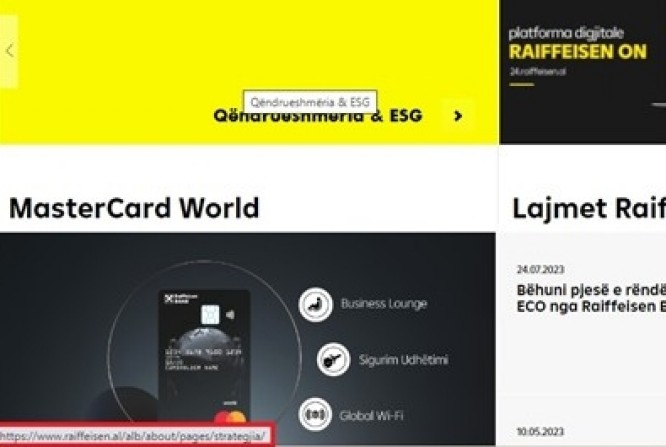
Make sure that the website's URL contains HTTPS and the padlock icon: Legitimate websites use HTTPS to encrypt your data during transmission, adding an extra layer of security. Look for the padlock icon in the address bar, indicating a secure connection.
Example of an insecure website:

Example of a secure website:

Safeguard your children from online deceit and content unsuitable for their age.
In this digital age that is evolving rapidly, the online safety of our children is a matter of particular importance.
By implementing these simple measures, each of us can create a safer digital environment where our children can explore and learn:
Limit exposure to electronic devices. Although technology can be educational and entertaining, excessive screen time can have negative effects on the well-being and online safety of our children. Consider setting daily time limits for electronic device use and encourage outdoor activities, reading books, and creative games to achieve a balanced and healthy development. It's important not to forget that the goal is not to eliminate technology but to teach our children to use it responsibly and safely.
Regularly update the operating system and installed programs on the devices used by your children. Updates often include important adjustments that help protect against potential online threats.
Use parental control options. Most devices, including iOS and Android devices, offer parental control configuration options that can help you manage your child's Internet experience. These controls are user-friendly and can be adapted to the specific age and interests of the children.